Each of the Essential Eight strategies has four maturity levels, which assist in implementation. Each level is based on mitigating increasing levels of adversary tradecraft (tools, tactics, techniques and procedures).
These are the last four mitigation strategies actioned to best put up a defence against threats.
5. APPLICATION CONTROL
Application control can be defined as ‘an approach in which only an explicitly defined set of trusted applications are allowed to execute on a given system’. When it comes to the Essential Eight, application control is one of the most effective strategies. But what is it exactly and how does it work?
Application control is a system that stops anything that isn’t a known requirement from your organisation from running. Previous malware systems were based around stopping malicious programs, but application control will stop any unnecessary or unapproved applications, putting up more protections between the system and potential threats.
When actioning application control, the ACSC recommends four steps to implementation:
- Identify the applications your organisation wishes to approve.
- Develop application control rules to ensure only approved applications can be executed.
- Maintain application control rules using a change management program.
- Validate application control rules on an annual or more frequent basis.
While an important and essential part of the ACSC’s data security control, application control is not a replacement for antivirus software. It’s considered a parallel application and part of the broader defence-in- depth strategy.
Maturity level one:
Organisations at Maturity Level One will focus effort on preventing the execution of executables, software libraries, scripts, installers, compiled HTML, HTML applications and control panel applets on workstations within standard user profiles and temporary folders used by the operating system.
6. CONFIGURE MICROSOFT OFFICE MACRO SETTINGS
This strategy is designed to effectively manage the risk of allowing macros in an organisation’s environment. Microsoft Office applications have the ability to execute a code that automates routine tasks inside of Office documents (such as Word, Excel and PowerPoint). These codes – also known as macros – are a common initial vector for an attacker to gain access to an organisation’s network.
When it comes to this particular strategy, it’s a simple and cost- effective strategy. The ACSC suggests organisations consider simply disabling all use of Microsoft Office macros. This allows an organisation to reach up to Maturity Level Three of the framework for this strategy.
Which macros should you trust?
It can be hard to determine just which macros to trust. The ACSC recommends all macros created by users and third parties be reviewed, assessed and assured to be safe before being implemented. In order to assess this, the ACSC recommends asking the following questions:
- Is there a business requirement for a particular macro?
- Has the macro been developed or provided by a trusted party?
- Has the macro been validated by a trustworthy and technically skilled party?
The different approaches for macro configuration:
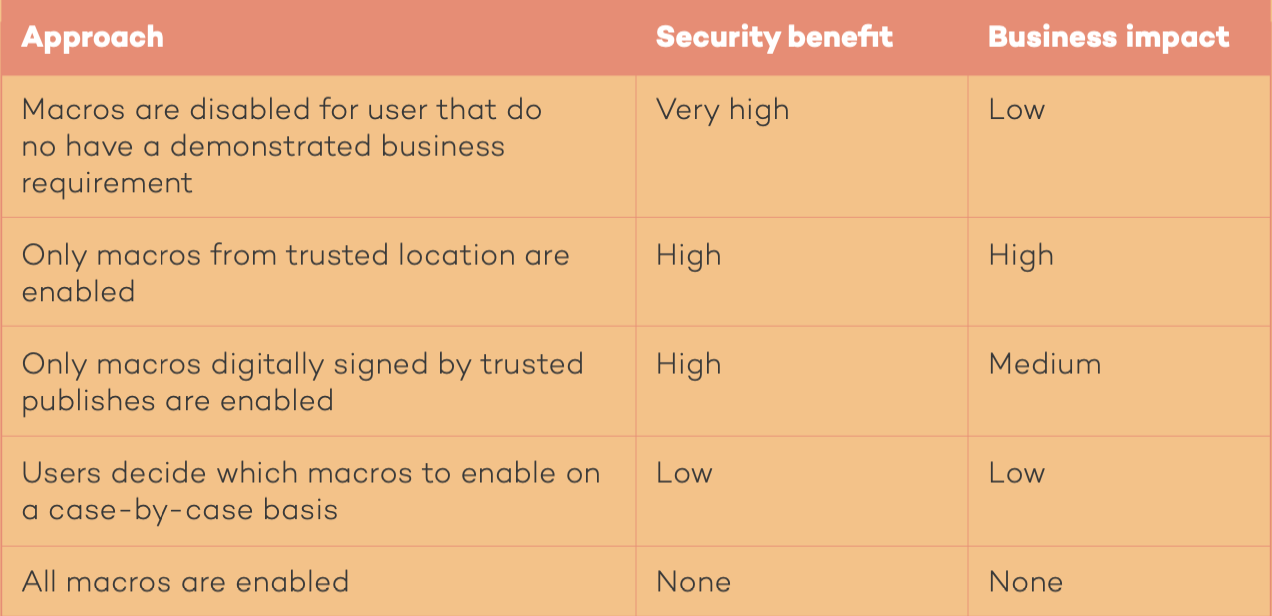
Maturity Level One:
Maturity Level One organisations must ensure that Microsoft Office macros are disabled for users that do not have a demonstrated business requirement. These users should block Microsoft Office macros in files originating from the internet, and enable macro antivirus scanning.
7. USER APPLICATION HARDENING
Cyberattacks often take place on a legitimate application, affecting its functionality and rewiring it for malicious purposes. User application hardening is designed to protect an organisation from a range of threats, including malicious websites, as well as advertisements running malicious scripts. Employing user application hardening will make it much harder for cybercriminals to explore vulnerabilities or at-risk functionality in your organisation’s applications.
